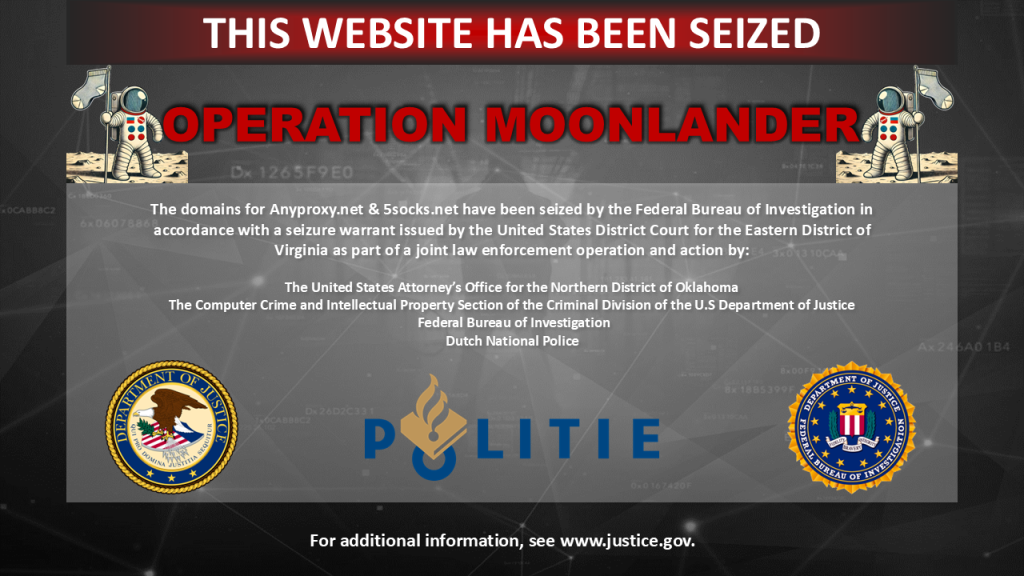
In a significant international cybersecurity operation, the FBI and Dutch National Police have successfully dismantled a sprawling botnet comprising over 7,000 compromised routers. Dubbed “Operation Moonlander,” this joint effort targeted two services—Anyproxy and 5Socks—that allegedly sold access to these hijacked devices, enabling cybercriminals to mask their identities and conduct illicit activities online.
The Operation
On May 7, 2025, law enforcement agencies seized the domains of Anyproxy and 5Socks, replacing their websites with notices indicating the takedown. The U.S. Department of Justice has indicted four individuals—three Russian nationals and one from Kazakhstan—for their roles in operating this botnet. These individuals are accused of exploiting vulnerabilities in outdated routers to build a network that served as a “residential proxy” service for cybercriminals.
The Threat
he botnet primarily targeted end-of-life routers from manufacturers like Linksys, Cisco, and Cradlepoint. These devices, no longer receiving security updates, were infected with variants of the “TheMoon” malware, granting attackers remote control. Once compromised, the routers were added to the botnet and sold as proxy nodes, allowing malicious actors to obfuscate their locations and activities.
Global Impact
The dismantled botnet had been operational for nearly two decades, posing a significant threat to global cybersecurity. By providing anonymity to cybercriminals, it facilitated a range of illicit activities, including data theft and espionage. The operation underscores the importance of international collaboration in combating cyber threats.
Recommendations
In light of this operation, the FBI advises users to:
- Replace outdated routers with models that receive regular security updates.
- Disable remote administration features on home networking devices.
- Regularly update firmware and change default passwords
By taking these steps, individuals can protect their devices from becoming part of malicious botnets.








Discussion about this post